Module: Deploy ADFS Load Balancing Services¶
In this module you will deploy simple load balancing of ADFS for internal users. No proxy services are needed for internal users.
Change Client to Point at BIG-IP Load Balancing Virtual Server¶
- Double click the BIG-IP ADFS Load Balancer desktop shortcut
- You should see that the HOSTS file now points ADFS at the load balancing virtual server (which is not yet created)
- Close any open Chrome incognito windows
- Open a new Chrome window if not already open.
- Right click the “ADFS Demo App shortcut” and open a new incognito window
- It should fail because you cannot access ADFS through the BIG-IP until you deploy the configuration.
- If it is still working, you may need to close Chrome and/or retry the HOSTS file shortcut.
Deploy ADFS iApp for ADFS Load Balancing¶
- Open the BIG-IP configuration interface
- Open Local Traffic -> Virtual Servers and notice nothing is deployed
- Open iApps -> Application Services -> Applications
- Click Create
Accept all default values except for those listed below.
- Name: adfs-lb
- Template: f5.microsoft_adfs.v1.2.0rc7
- SSL Encryption
- How should the BIG-IP system handle SSL traffic?
- Encrypted traffic is forwarded without decryption (SSL pass-through)
- How should the BIG-IP system handle SSL traffic?
SSL Pass-Through is chosen because Microsoft requires it for supported load balancing of ADFS. SSL Bridging breaks the connectivity between WAP servers and ADFS servers because client certificate authentication is required. You can use SSL Bridging if you will not point WAP servers at your deployment but following Microsoft’s guidelines and using SSL Pass-Through is recommended.
- High Availability
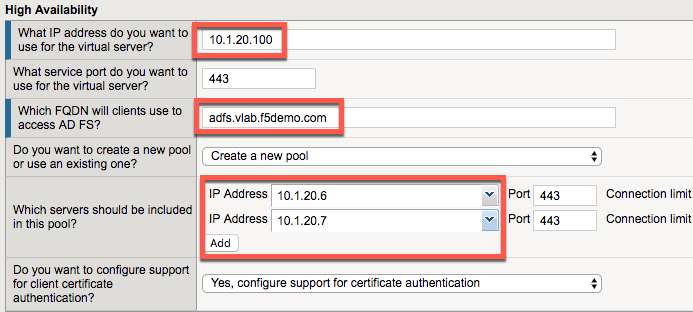
- What IP address do you want to use for the virtual server?
- 10.1.20.100
- What IP address do you want to use for the virtual server?
10.1.20.x is the internal network in this environment.
- Which FQDN will clients use to access AD FS?
- adfs.vlab.f5demo.com
- Which servers should be included in this pool?
- 10.1.20.6
- Click Add
- 10.1.20.7
- Click Finished
Test the ADFS Load Balancing Functionality¶
- Close any open Chrome incognito windows
- Open a new Chrome window if not already open
- Right click the “ADFS Demo App” shortcut and open in an incognito window
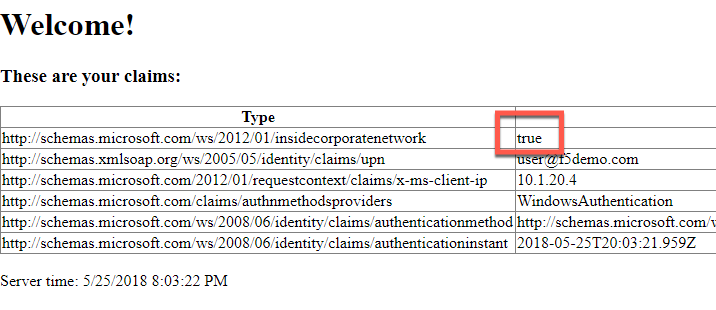
- You should see a set of claims displayed in the claims app at app.vlab.f5demo.com
- Note that ADFS is still identifying the user as inside the corporate network because the user did not go through an MS-ADFSPIP compliant proxy solution.
- What happened:
- You made a request to App
- App redirected you to ADFS for authentication
- The BIG-IP received the request and load balanced it to one of the ADFS servers (this is the only change from last time)
- ADFS authenticated you automatically with Windows Integrated Authentication with your domain joined computer
- ADFS redirected you back to App with a WS-Fed assertion
- App validated the assertion and displayed the claims it received from ADFS
Review the ADFS Load Balancing Configuration¶
- Go to Local Traffic -> Virtual Servers
- Notice there are two deployed, one on port 443 and one on port 49443
- 443 is for ADFS traffic
- Pool members use port 443
- 49443 is for client certificate auth support
- Pool members use port 49443
- 443 is for ADFS traffic